Sometimes, particularly when dealing with a system perimeter, there’s very little attack surface to deal with. You may find yourself with not much more than boring old XSS to poke at. We feel your pain. The good news is that it isn’t all doom and gloom. XSS can be leveraged in some fairly interesting ways. Enter our XSS payloads repository.
The challenge
Picture the following scenario. You’re faced with some persistent Cross Site Scripting on an employers HR web application, and very little else.
You can alert(1) your way into redundancy or you can gain access to the internal network. While potentially helpful, using a XSS framework is overkill, and besides, you’re fairly sure it’ll trip an alarm. You rummage around in your sack of XSS payloads and decide to plant an attack that turns every URL into a UNC path. You’re fairly sure that the corporate infrastructure has solid egress rules in place, but perhaps those remote workers are not on a no-split VPN… you set up an SMB listener, leave your payload and go and have a coffee.
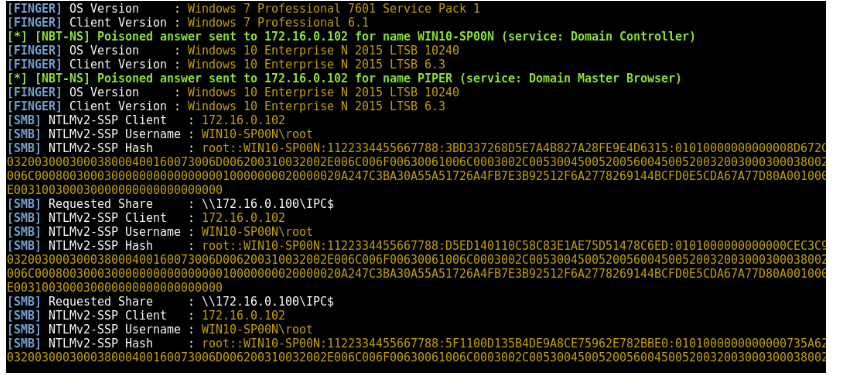
NTLM hashes
When you return, you have a small number of NTLM hashes. Password complexity is in place, but people go to extreme lengths to choose weak passwords. A short blast of hashcat later and you’ve cracked a few Password1 and Summer2016’s. As with most corporate perimeters, there are a number of employee services facing the internet. OWA, SSL-VPN, Citrix… on and on it goes. Most should not be on the internet and all should require 2FA. Neither are true. So much for alert(1).
As attackers, we typically want to achieve depth of penetration. Without significant exploitation and post exploitation activities, it’s unlikely that we will gain access to our target assets. It’s easy to overlook common and boring vulnerabilities, but they’re called vulnerabilities for a reason.
The payloads
We have started to curate some of our favourite XSS payloads, which are all stand alone, lightweight and easy to use. Some of the functionality includes:
- Turning hyperlinks into UNC paths
- Popping up modal authentication boxes
- Local network port scanning
- Victim DOM theft
- …plenty more besides
You can find the payloads here:
![]() GitHub: https://github.com/nettitude/xss_payloads
GitHub: https://github.com/nettitude/xss_payloads
We intend to give this repository some continued love and, over time, you’ll find more and more payloads appearing. This one is just a bit of fun and we absolutely welcome contributions!



