LRQA identified two stored Cross Site Scripting (XSS) vulnerabilities within Vanderbilt REDCap. These have been assigned CVE-2022-24004 & CVE-2022-24127.
REDCap is a web application which allows the creation and management of online surveys for research purposes. Version 12.0.11 and below allows a remote authenticated attacker to inject arbitrary JavaScript or HTML via the Messenger functionality and the administration interface.
CVE-2022-24004 – Proof of Concept
REDCap has a built in messenger function which allows all registered users to communicate within the application. Each conversation created has a title which can only be edited by the user which originally created the conversation. The input field where this title can be edited does not filter input and as a result, it is possible to inject malicious JavaScript and HTML.
Example POST data sent to Messenger_ajax.php:
This payload will then trigger in the browser where the messenger sidebar is toggled of any user which is a participant of the conversation. The following screenshot shows that the payload is injected into the data-tooltip parameter of the h4 tag.
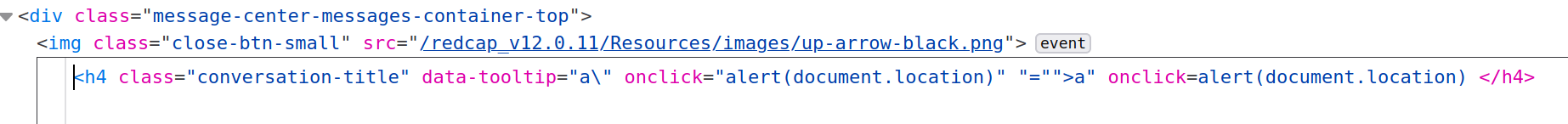
For this simple proof of concept, the user would have to click on the message title, resulting in the execution of a JavaScript alert.
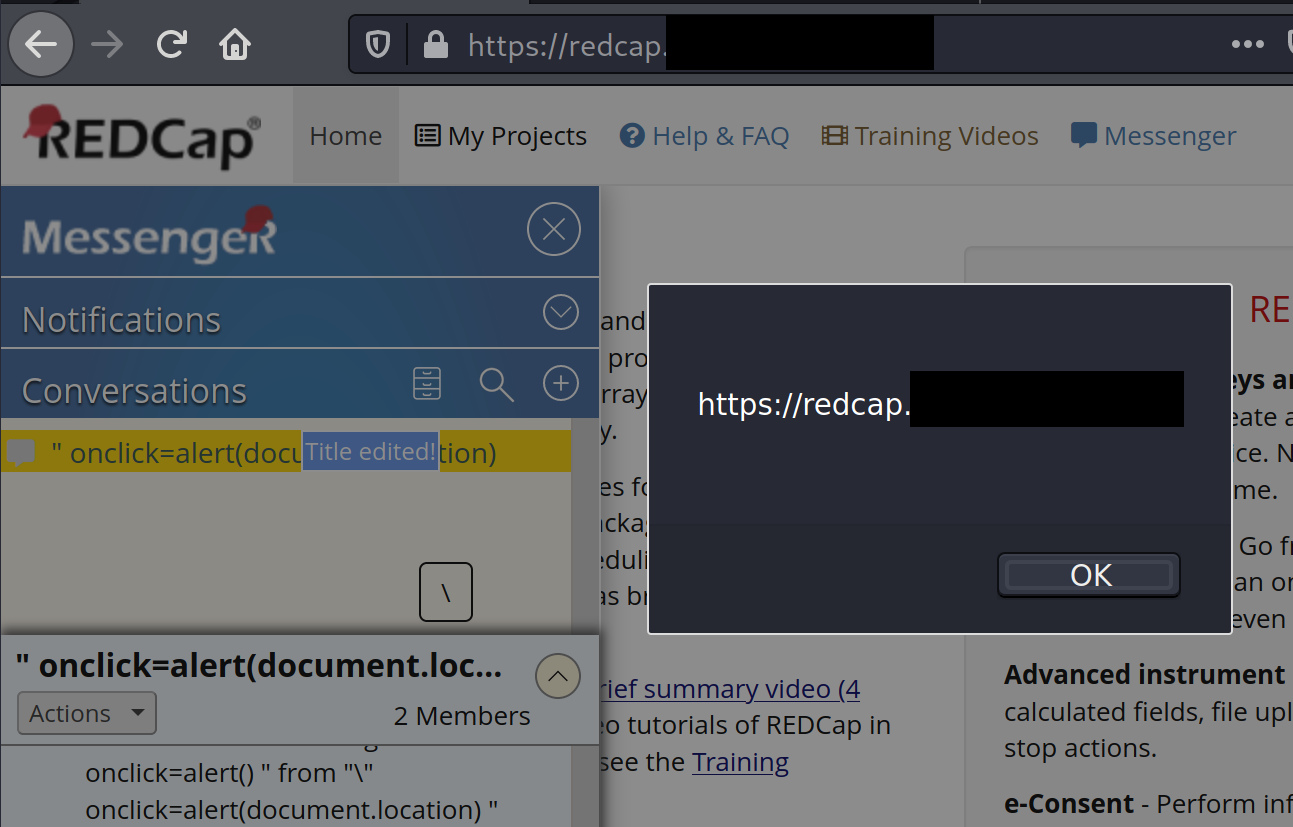
The impact of this vulnerability could lead to the disclosure of sensitive application and survey data. Given that the messenger functionality will autocomplete usernames after providing the first character, it is possible to see how an attacker could create a conversation with all application users to maximise chances of compromising application data from an administrator user.
LRQA demonstrated the impact of this to the application vendor by further improving the proof of concept to automatically trigger on page load and scrape the contents of the users screen, sending this data to a remote server.
CVE-2022-24004 – Affected Component
This vulnerability affects REDCap version 12.0.11. Previous versions may also be affected.
- Vulnerable page: Messenger_ajax.php
- Vulnerable parameter: new_title
CVE-2022-24127 – Proof of Concept
In the project administration section of the application, admin users that have permissions to modify a project can modify the project title. The input field where this value is modified does not filter input and as a result, it is possible to inject malicious JavaScript and HTML.
Example POST Data sent to edit_project_settings.php:
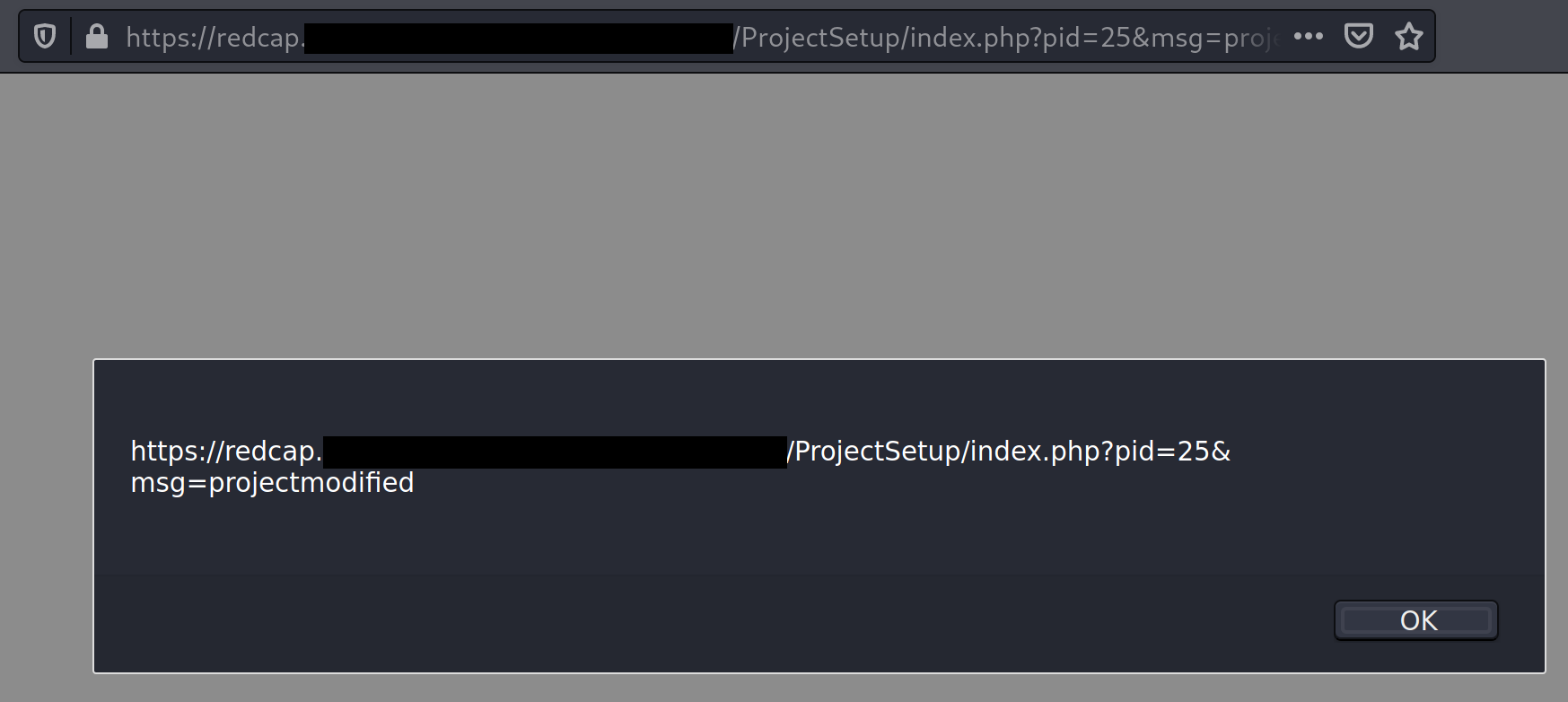
Once the project title is modified, the user is returned to the project administration home page where the payload immediately triggers and will continue to be executed across all administration pages related to the project.
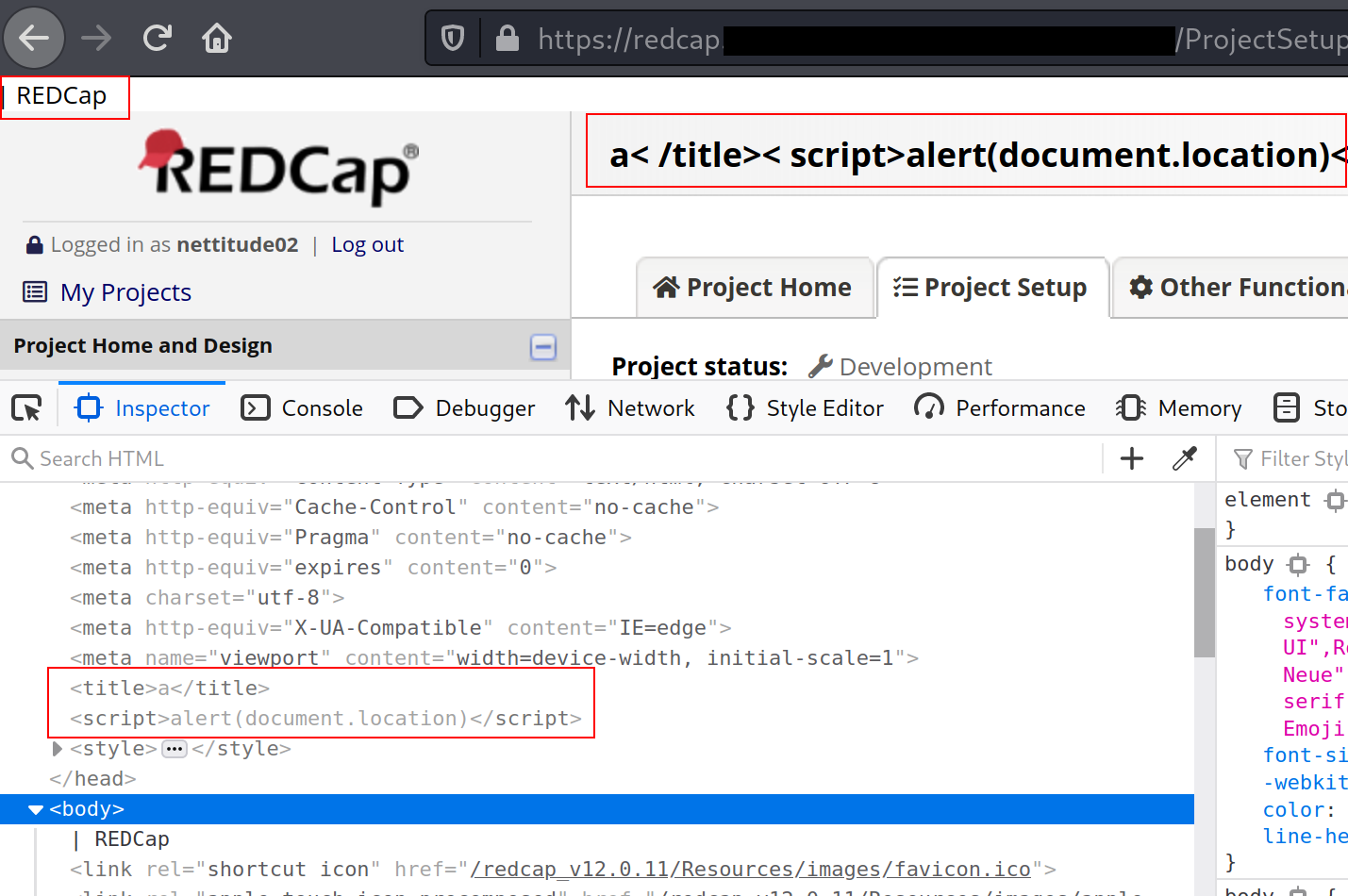
This code execution is triggered due to the project title being reflected in the page <title> tag. If a user enters a value which first closes the tag, then any further HTML or JavaScript can be executed as shown in the following screenshot.
The impact this vulnerability is reduced because it would require the attacker to have existing access as a user with project administration permissions. An attacker could potentially exploit this issue to redirect the user to a malicious website controlled by the attacker, which may ultimately lead to credential harvesting or the downloading of malware.
CVE-2022-24127 – Affected Component
This vulnerability affects REDCap version 12.0.11. Previous versions may also be affected.
- Vulnerable page: edit_project_settings.php
- Vulnerable parameter: app_title
Conclusion
All areas of a web application which accept and store user input should not be trusted. Appropriate measures should be taken to sanitize or encode data before being shown in a later browser response.
LRQA contacted Vanderbilt to disclose these vulnerabilities. Remediation was put in place almost immediately post-disclosure and a remediated version (12.0.13) was promptly released.

Timeline – CVE-2022-24004
- Discovered by LRQA: 25 January 2022
- Vendor informed: 26 January 2022
- CVE Assigned: 26 January 2022
- Vendor fix released: 28 January 2022
- LRQA Blog: 15 June 2022
Timeline – CVE-2022-24127
- Discovered by LRQA: 28 January 2022
- Vendor informed: 28 January 2022
- Vendor fix released: 28 January 2022
- CVE assigned: 29 January 2022
- LRQA Blog: 15 June 2022



