Overview
Two years after first gaining notoriety, the Pony Botnet remains very active. The malware is primarily targeted at the theft of user credentials from applications such as web browsers and email applications, for example, Outlook. Pony is also capable of stealing a victim’s bitcoin wallet.
A typical attack is executed through the use of a phishing e-mail containing a malicious attachment.
One of the most worrying aspects of Pony is that the source code is fully available online and is free to download, so anyone with the correct level of knowledge and motivation could potentially set up a botnet.
I recently investigated a malware sample that turned out to be Pony malware. Below is a brief summary of the analysis.
Analysis
The malicious binary came in the form of a heavily obfuscated .NET binary and was named so that it appeared as a spreadsheet – presumably to trick the victim into opening it – however, the attackers had not bothered to replace the application icon with that of an Excel spreadsheet, so this ruse would not fool everyone.
MD5: 87fc4d453ca983a6a1b2fe92d3bf4a71
SHA-1: b4dbd3de13b492aa12f3030bcd04be2d717945a0
Analysis in Cuckoo sandbox didn’t provide any insight into the purpose of the executable, so I spent some time investigating the malware.
Using a .NET decompiler showed that the binary had been heavily obfuscated. This is clear as all of the class names have been replaced with single characters and the code consists of many switch statements and magic numbers.
There was clearly no point in spending time trying to analyse this code, so I took the path of least resistance, which was to use Rohitab API Monitor[1].
The malware launches a child process “RegAsm.exe”. RegAsm is a non-malicious .NET executable that is provided by Microsoft as part of the .NET framework, so it is present on most modern computers running Windows. Usually RegAsm is used for registering .NET assemblies, however, the malware uses this executable as the host for malicious code, which is injected into the RegAsm.
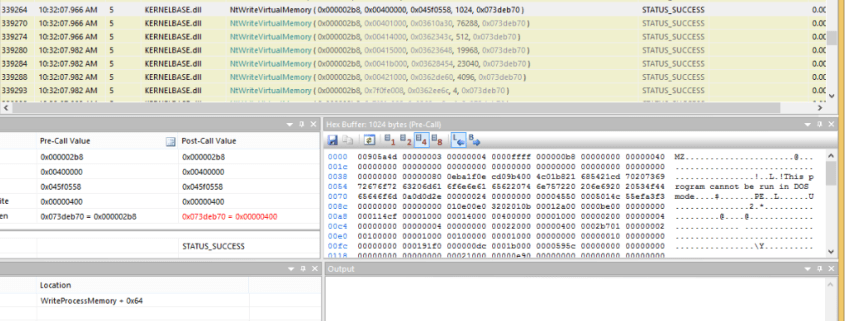
Firstly, it creates the RegAsm process with all of its threads suspended; this is achieved by using the “CREATE_SUSPENDED” flag for CreateProcess. API monitor allows us to capture this activity:
Once the RegAsm process has been created, the malware decodes an obfuscated binary payload, contained within its .NET resources and ten proceeds to inject this into the newly created “RegAsm.exe” process by using WriteProcessMemory.
The malware is mapped into RegAsm at a base address of 0x00400000 and the thread context of RegAsm’s main thread is then modified by the malware in order to begin execution at the malicious code entry point.
This effectively turns RegAsm into an empty shell, within which the malicious code is transplanted, transforming a benign executable into a malicious one. The malware then resumes execution of RegAsm in order to start payload.
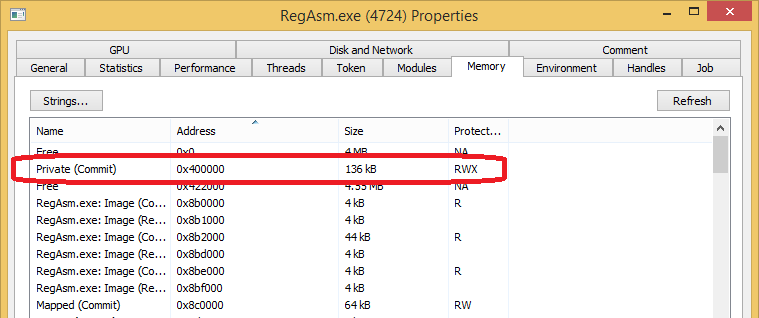
If we examine the RegAsm process with Process Hacker[2] we can see virtual memory at 0x00400000 with read, write and execute permissions. Memory with read, write and execute permissions is suspicious in its self as it commonly indicates injected code inside a process.
Using Process Hacker, the malicious executable code was then carved from the RegAsm memory and investigated further.
The following strings were found in the executable:
These are an indicative fingerprint of the Pony Botnet[3] client which reached notoriety in July and December 2013.
Further analysis of the binary confirms this to be Pony, which is used by cyber criminals to steal credentials for a number of popular applications, including Bitcoin wallets.
The following software credentials can be stolen by Pony running on the victim’s computer:
FAR Manager, Total Commander, WS_FTP, CuteFTP, FlashFXP, FileZilla, FTP Commander, BulletProof FTP, SmartFTP, TurboFTP, FFFTP, CoffeeCup FTP / Sitemapper, CoreFTP, FTP Explorer, Frigate3 FTP, SecureFX, UltraFXP, FTPRush, WebSitePublisher, BitKinex, ExpanDrive, ClassicFTP, Fling, SoftX, Directory Opus, FreeFTP / DirectFTP, LeapFTP, WinSCP, 32bit FTP, NetDrive, WebDrive, FTP Control, Opera, WiseFTP, FTP Voyager, Firefox, FireFTP, SeaMonkey, Flock, Mozilla, LeechFTP, Odin Secure FTP Expert, WinFTP, FTP Surfer, FTPGetter, ALFTP, Internet Explorer, Dreamweaver, DeluxeFTP, Google Chrome, Chromium / SRWare Iron, ChromePlus, Bromium (Yandex Chrome), Nichrome, Comodo Dragon, RockMelt, K-Meleon, Epic, Staff-FTP, AceFTP, Global Downloader, FreshFTP, BlazeFTP, NETFile, GoFTP, 3D-FTP, Easy FTP, Xftp, RDP, FTP Now, Robo-FTP, Certificate, LinasFTP, Cyberduck, Putty, Notepad++, CoffeeCup Visual Site Designer, FTPShell, FTPInfo, NexusFile, FastStone Browser, CoolNovo, WinZip, Yandex.Internet / Ya.Browser, MyFTP, sherrod FTP, NovaFTP, Windows Mail, Windows Live Mail, Becky!, Pocomail, IncrediMail, The Bat!, Outlook, Thunderbird, FastTrackFTP, Bitcoin, Electrum, MultiBit, FTP Disk, Litecoin, Namecoin, Terracoin, Bitcoin Armory, PPCoin (Peercoin), Primecoin, Feathercoin, NovaCoin, Freicoin, Devcoin, Frankocoin, ProtoShares, MegaCoin, Quarkcoin, Worldcoin, Infinitecoin, Ixcoin, Anoncoin, BBQcoin, Digitalcoin, Mincoin, Goldcoin, Yacoin, Zetacoin, Fastcoin, I0coin, Tagcoin, Bytecoin, Florincoin, Phoenixcoin, Luckycoin, Craftcoin, Junkcoin.
Stolen information for these applications is sent back to the Pony command and control server.
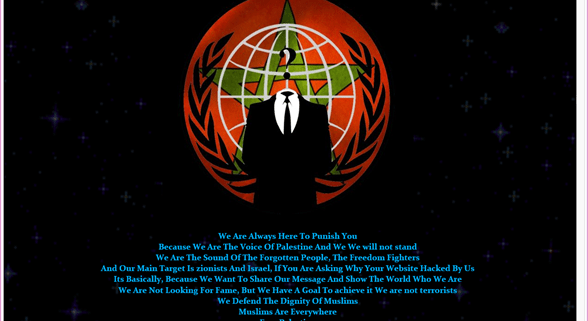
Interestingly, the command and control website that malware beacons out to, purports to have been hacked; visitors to the beacon web site are presented with the following web page:
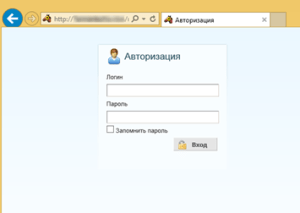
Deeper investigation of the website reveals a Pony Malware administration login page:
Conclusion
Several years after first being discovered, Pony is still in use by cyber-criminal organisations.
To protect against Pony malware, we recommend that computer users are educated about the danger of opening attachments from unknown sources.
Antivirus should always be kept up to date, however, malware authors often change the signatures of their malware regularly using obfuscation and mutation techniques. This sometimes allows them to bypass anti-virus (AV), so it is also vital that network activity is monitored 24/7 to ensure that botnet communication can be observed and addressed in a timely manner.
The use of two factor authentication is also recommended, so that if Pony does steal passwords they are useless without the second authentication method.
Finally, avoid using the same password for each service that you log in to. This way, the damage can be minimised if Pony does steal your credentials.
References
- Rohitab API Monitor
http://www.rohitab.com/apimonitor
- Process hacker
http://processhacker.sourceforge.net/
- Pony Botnet
https://www.trustwave.com/Resources/SpiderLabs-Blog/Look-What-I-Found–It-s-a-Pony!/
To contact Nettitude’s editor, please email media@nettitude.com.