Nettitude has discovered that the iArtist application is vulnerable to CWE-290 Authentication Bypass by Spoofing. This flaw can be leveraged to remove the need to supply valid credentials when uploading a presentation.
Additionally, the Signage Station system suffers from CWE-768 Use of Hard-coded Credentials. This grants access to the host NAS FTP service and can also be used to upgrade CVE-2015-6022 to an unauthenticated exploit.
Introduction
In a previous blog post it was shown that a low privilege Signage Station user could remotely upload a web-shell and thus significantly elevate their access to the host NAS system. However, the outlined steps still required a valid username and password, somewhat diminishing the impact.
Arguably remote unauthenticated vulnerabilities pose the greatest risk to the security of a system. Typically an attacker will only need connectivity in order to bypass any perimeter security mechanisms and gain access to the system. With this in mind, I began to examine the system to identify a means of circumventing the authentication process.
Vulnerability 1 – Authentication Bypass by Spoofing
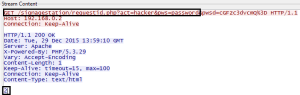
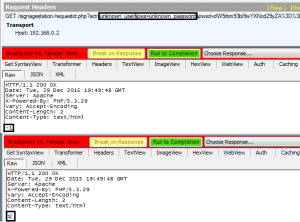
Although the uploading of presentations takes place over File Transfer Protocol (FTP), user authentication occurs over HTTP. The iArtist client makes a GET request to http://<ip_address>/signagestation/requestid.php, passing the username and password via URL parameters. In response, the Signage Station server returns either negative 1 when authentication has failed or a positive integer when authentication has succeeded.
By intercepting a failed response and changing the value to 1, it is possible to initiate and successfully complete an iArtist presentation upload without valid credentials.
This mechanism does not authenticate the FTP upload, rather it controls whether the iArtist application will initiate and complete one.
Vulnerability 2 – Use of Hard-Coded Credentials
The authentication of the FTP process takes place with hardcoded credentials. The iArtist application and Signage Station App both ship with these credentials and as such, grant a suitably informed adversary the ability to:
- Access the system FTP server on the host NAS device
- Upload a presentation, malicious or otherwise
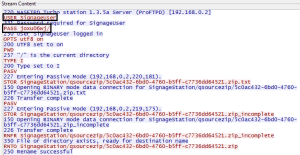
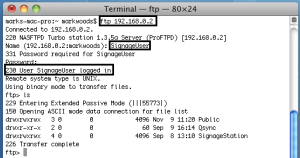
These credentials can be observed on the wire when iArtist uploads a presentation.
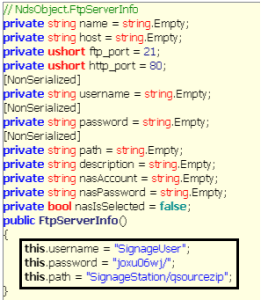
They can also be extracted from iArtist via reverse-engineering.
An account with these credentials can also be seen on the host NAS. By hashing the password we can see it matches the SignageUser password hash, an account created when the Signage Station App was installed.
Finally, we can use the credential with any FTP client to access the NAS FTP server.
Summary
Signage Station (2.0.0.3) hosted on the QNAP App Center is vulnerable to CWE-290 Authentication Bypass by Spoofing and CWE-768 Use of Hard-coded Credentials. These each independently grant a remote unauthenticated user the opportunity to upload a presentation to the Signage Station App. They can therefore be used in conjunction with CVE-2015-6022 to gain remote unauthenticated access, as a member of the Administrator’s group, to the host NAS device. System users should contact the vendor for a fix.
In the third and final part of this series we will see how the iArtist application introduces a significant vulnerability on to the host Windows system.
The release of this information has followed the responsible disclosure model. All research has been forwarded to QNAP and the date of disclosure mutually agreed. CERT has been informed and is tracking this issue.
Timeline
- QNAP informed via email 19/10/2015
- Reported to cert.org 19/10/2015
- Authentication bypass by spoofing issue assigned CVE-2015-6036 21/10/2015
- Use of hard-coded credentials issue assigned CVE-2015-7261 30/11/2015
- Proof of concept completed 13/12/2015
- Disclosure date extended 11/01/2016
- Vulnerabilities disclosed 25/02/2016
References
- Vulnerability Note – http://www.kb.cert.org/vuls/id/444472
- QNAP Signage Station – https://www.qnap.com/event/station/en-uk/signage.php
- CVE-2015-6036 QNAP Signage Station – http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2015-6036
- CVE-2015-7261 QNAP Signage Station – http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2015-7261
- ILSpy – http://ilspy.net/
- Wireshark – https://www.wireshark.org/
- Fiddler 2 – http://www.telerik.com/fiddler
To contact Nettitude’s editor, please email media@nettitude.com.