“Historically, security tools worked in silos. The endpoint tool didn’t talk to the identity tool. This gap is where attackers – and our red teams – usually thrive.”
One thing you learn after spending enough time in the cyber industry is to be sceptical of “perfect” scores.
In the lab, variables are controlled. Traffic is predictable. The "adversary" follows a script. So, when CrowdStrike recently announced 100% detection and protection in the 2025 MITRE ATT&CK Enterprise Evaluations, my first instinct wasn't blind applause. It was to ask: “That’s great for the scoreboard, but how does it handle a rainy Tuesday in a complex, legacy-ridden corporate network?”
I’m writing this not just as a partner, but as an observer of the cat-and-mouse game played out daily in our operations centre. At LRQA, we wear both hats. We defend networks via our MDR and SOC services, but we also attack them. Our red teamers spend their days simulating advanced adversaries (like the MenuPass and BlackCat groups emulated in this year’s MITRE tests).
We don’t choose our partners based on marketing gloss. We choose them based on who gives our offensive teams the biggest headache.
Here is the honest reality of what happens when "perfect" lab results meet the messy real world.
The "Groan" in the room
There is a specific dynamic I see often during engagement kick-offs or mid-operation debriefs. Our red teamers – highly skilled operators who live for the challenge – will be outlining their reconnaissance. Then, someone mentions the target is running CrowdStrike Falcon.
The mood in the room shifts. There is almost a collective sigh.
Why? Because our red teamers know their job just got harder. In our experience, CrowdStrike doesn’t just rely on matching known bad signatures. If that were the case, our team could simply recompile their tools or change a file hash to bypass it. Instead, the platform looks at behaviour.
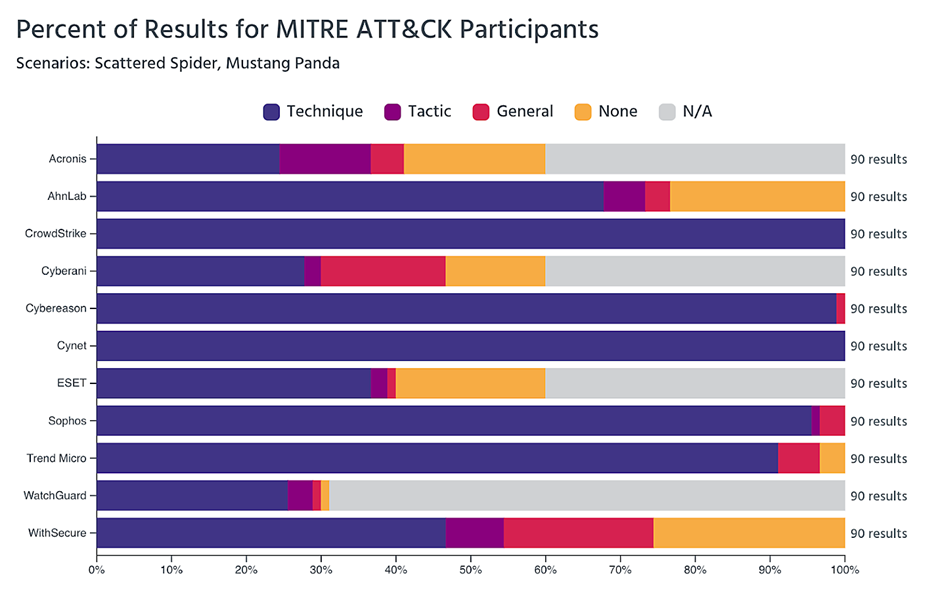
Figure 1: The depth of visibility matters. As shown above, CrowdStrike secured 100% visibility across tactics and techniques (the purple bars), leaving no gaps for attackers to hide in.
In the MITRE evaluation, CrowdStrike blocked 100% of the attacks. For our red teams, this translates to friction. When they try to "live off the land" – abusing legitimate administrative tools like PowerShell or WMI to move laterally – Falcon tends to spot the intent, not just the tool. It forces our operators to slow down, be quieter, and burn significantly more time to achieve objectives that might take minutes in a less protected environment.
Crossing domains: The new battleground
One of the most critical aspects of the 2025 MITRE evaluation was its focus on cross-domain attacks – specifically the jump between Endpoint, Identity, and Cloud.
This mirrors exactly what our offensive teams are targeting. They tell me constantly that the days of "land on laptop, stay on laptop" are over. They want the cloud infrastructure. They want the identity provider.
Historically, security tools worked in silos. The endpoint tool didn’t talk to the identity tool. This gap is where attackers – and our red teams – usually thrive. They might steal credentials from an endpoint (Endpoint) and use them to log into Azure or AWS (Cloud). To a siloed defence, this looks like two separate, legitimate events.
CrowdStrike’s ability to stitch these domains together is a major reason it sits at the core of our recommendations. When the platform correlates a process injection on a workstation with a subsequent anomalous login to the cloud console, it burns the attacker’s cover. That "stitched" visibility is often the difference between a contained incident and a headline-grabbing breach.
The Blue Team perspective: Silence is golden
Switching hats to our defensive operations, there is another reason I endorse CrowdStrike for our clients: Signal-to-Noise Ratio.
A "100% detection" score is dangerous if it comes with 500% false positives. Any tool can detect an attack if it alerts on everything that moves. But that renders a SOC useless, burying analysts under a mountain of junk data.
Our SOC favours CrowdStrike because the alerts are generally high-fidelity. When the Falcon console lights up, it’s usually for a reason. This allows our team to focus on hunting and response, rather than spending hours tuning out noise.
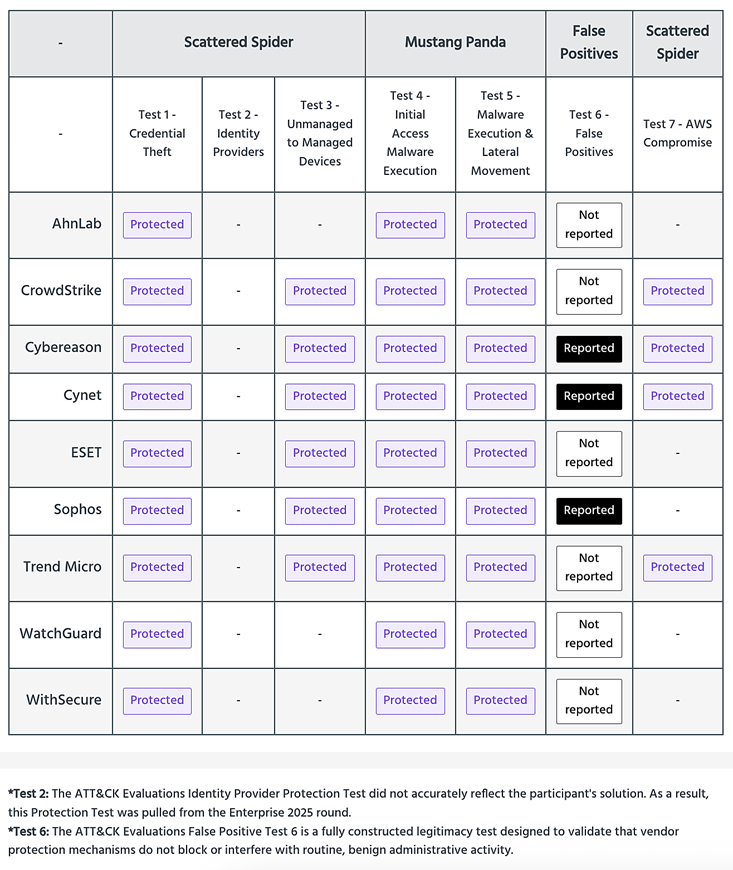
Figure 2: Protection without the noise. The MITRE results highlight consistent protection across the kill chain (Credential Theft, Lateral Movement) while maintaining a clean record on false positives (Test 6).
In the MITRE test, CrowdStrike achieved its detection score with zero false positives. While no tool is perfect in a chaotic production environment, this efficiency is critical. It reduces "alert fatigue," keeping our analysts sharp for when a real threat actor (or one of our red teams) actually comes knocking.
A note on "Silver Bullets"
It is important to end on a note of pragmatism. Is CrowdStrike a silver bullet? No. There is no such thing in our industry.
You can buy the best EDR on the market, but if you deploy it with a "default allow" policy, fail to enable the identity protection modules, or ignore the alerts it generates, our red team will still get through.
Technology is only one leg of the stool. It must be supported by:
- People: Skilled analysts who know how to interpret the data.
- Process: Rigorous hygiene, patching, and incident response playbooks.
However, when CrowdStrike is implemented correctly and monitored by a capable team, it raises the cost of the attack astronomically. It forces the adversary to work harder, riskier and slower. And in our game, time is the defender’s greatest asset.
The Verdict
We partner with CrowdStrike not because they won a contest, but because we see first-hand how they force our offensive teams to bring their A-game. They make the job harder for attackers, which means they make your organisation safer.
In an industry full of noise, that is the only metric that truly matters.
Is your EDR actually working? Buying the tool is step one. Knowing it works against a human adversary is step two. Contact LRQA today to discuss how we can validate your defences or explore how our MDR services can help you get the most out of your security investment.
References
CrowdStrike Achieves 100%s in 2025 MITRE ATT&CK Enterprise Evaluation










